In the modern digital landscape, where nearly every interaction is conducted online, businesses face a constant battle to protect themselves from fraudulent users, cybercriminals, and malicious actors who try to disguise their identities. One of the most common methods these individuals employ is hiding behind proxies, VPNs, or the TOR network to mask their real IP address and location. While these tools can have legitimate uses for privacy and data protection, they are also widely exploited to commit fraud, launch cyberattacks, and bypass security measures. With IPQualityScore, you can accurately detect proxies, VPNs, and TOR network usage in real time to block high-risk traffic, prevent fraud, and secure your platform against malicious activity. This makes the ability to accurately detect proxies, VPNs, and TOR network activity not just an optional security layer but a critical necessity for organizations across all industries.
Why Proxies, VPNs, and TOR Are Used
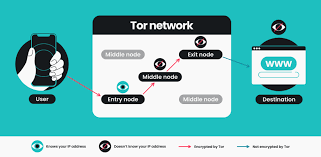
Understanding why proxies, VPNs, and the TOR network are used helps highlight the importance of detection. A proxy acts as an intermediary between the user and the internet, masking the original IP address. A VPN, or Virtual Private Network, encrypts internet traffic and routes it through servers worldwide, making the user appear as if they are in a different geographic location. TOR, short for The Onion Router, goes a step further by routing traffic through multiple nodes in a layered fashion, making it extremely difficult to trace activity back to the user. While these technologies can provide valuable privacy and protection for everyday users, cybercriminals use them to bypass geolocation restrictions, conduct fraudulent transactions, hide their identity when attacking networks, or create fake accounts en masse.
The Risks of Not Detecting Masked Connections
Failing to detect proxies, VPNs, and TOR connections exposes businesses to a wide array of risks. Fraudsters can easily create multiple accounts using masked IP addresses to exploit promotions, commit payment fraud, or carry out identity theft. E-commerce businesses, for example, face chargebacks when fraudulent purchases are made using stolen credit cards hidden behind VPNs. Similarly, social media platforms or online marketplaces become vulnerable to fake account creation, which can skew user metrics, spread misinformation, or even facilitate scams. Beyond fraud, masked connections can also be used to bypass regional restrictions on digital services, violating licensing agreements or compliance requirements. For financial institutions or businesses operating in regulated industries, failing to detect such activity can result in severe penalties or reputational damage.
Strengthening Fraud Prevention with Detection
Detecting proxies, VPNs, and TOR network usage empowers businesses to add a powerful layer of protection against fraud. When suspicious connections are flagged in real time, organizations can enforce stricter verification measures, such as two-factor authentication or identity checks, to ensure the legitimacy of the user. For instance, if a login attempt originates from a high-risk VPN IP address while the user’s account normally logs in from a specific city, this anomaly can trigger alerts or temporarily block access. By stopping fraud attempts before they escalate, businesses save money, maintain customer trust, and safeguard their platforms from abuse.
Enhancing Customer Trust and Security
Customers expect the businesses they interact with to provide secure and reliable services. By actively detecting proxies, VPNs, and TOR traffic, organizations can assure their legitimate users that their platforms are protected from malicious activity. Fraudulent activity not only harms businesses financially but also undermines customer confidence, especially when accounts are compromised or fraudulent transactions slip through undetected. On the other hand, by showing a commitment to robust security measures, businesses build stronger trust and loyalty with their customers, creating a safer digital environment for everyone involved.
Role in Regulatory Compliance
For industries that handle sensitive information, such as finance, healthcare, and telecommunications, compliance with data security and anti-fraud regulations is mandatory. Proxies and VPNs often mask the true geographic location of users, which can lead to regulatory breaches if users from restricted regions gain unauthorized access to services. The TOR network, in particular, is associated with illicit activities ranging from money laundering to cybercrime operations. By detecting and blocking these connections, businesses not only protect themselves but also demonstrate due diligence in meeting regulatory standards like GDPR, PCI DSS, and AML/KYC requirements. This reduces the risk of audits, fines, and legal challenges that could arise from overlooking suspicious activity.
Data Accuracy and Business Intelligence
Accurate user data is vital for businesses to make informed decisions. Proxies, VPNs, and TOR connections distort this accuracy by obscuring the true source of traffic. For marketing teams, this can lead to wasted budgets targeting the wrong regions or skewed campaign results. For operations teams, it can complicate analysis of user behavior, making it difficult to detect patterns and trends. By detecting and filtering out masked connections, businesses ensure that the data they collect is reliable and actionable. This not only improves marketing ROI but also enhances strategic planning across the organization.
Balancing Security and User Privacy
While detection is critical, businesses must also balance it with respect for user privacy. Not every proxy or VPN user is malicious; many individuals use these tools for legitimate reasons, such as protecting personal information or accessing services securely on public Wi-Fi. The goal is not necessarily to block all connections from these sources but to evaluate them intelligently. Advanced detection solutions often provide risk scoring, allowing businesses to differentiate between high-risk and low-risk users. By using this nuanced approach, organizations can maintain strong security without alienating genuine users who prioritize privacy.
Leveraging Technology for Effective Detection
Detecting proxies, VPNs, and TOR usage requires advanced technology and up-to-date intelligence. Solutions powered by real-time databases and machine learning models can identify suspicious IP addresses, analyze traffic patterns, and assign risk levels based on historical abuse data. These tools often integrate seamlessly via APIs, making it easy for businesses to incorporate them into existing workflows such as login verification, transaction monitoring, or account creation. With global coverage and continuous updates, such systems ensure that even newly deployed VPN servers or TOR exit nodes are identified quickly, minimizing the window of opportunity for fraudsters.
Conclusion
The importance of detecting proxies, VPNs, and TOR network activity cannot be overstated in a world where online fraud and cybercrime are growing at unprecedented rates. These technologies, while useful for legitimate privacy protection, pose significant risks when abused by malicious actors. By deploying effective detection systems, businesses can reduce fraud, maintain compliance, protect their data integrity, and foster stronger trust with customers. As fraud tactics become more advanced, proactive detection becomes not just a security measure but a competitive advantage. Organizations that embrace this approach will be better equipped to operate safely, confidently, and profitably in the digital era.





